Multi-Issue Authentication (MFA) is used so as to add one other safety layer to the IAM accounts/identities. AWS permits customers so as to add MFA to their accounts to guard their assets much more. AWS CLI is one other technique to handle AWS assets that can be protected via MFA.
This information will clarify methods to use MFA with AWS CLI.
How you can Use MFA with AWS CLI?
Go to the Id and Entry Administration (IAM) from the AWS console and click on on the “Customers” web page:
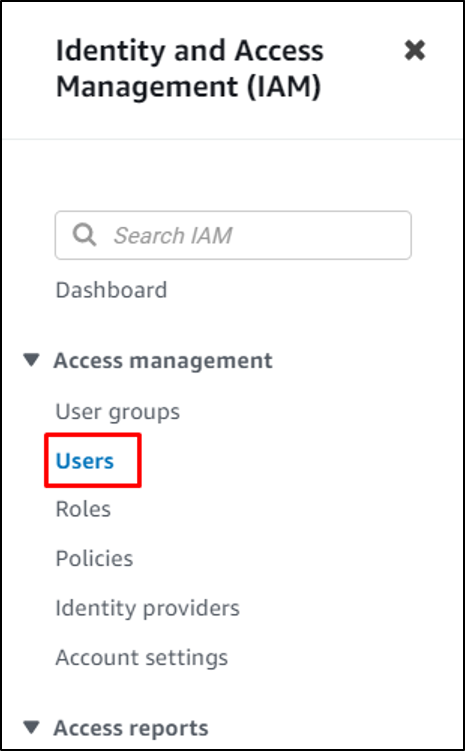
Choose the profile by clicking on its identify:
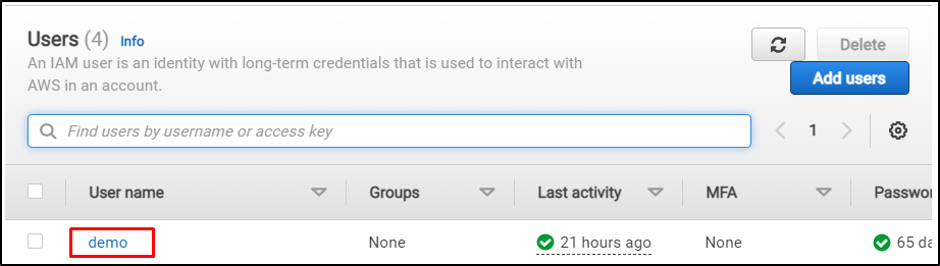
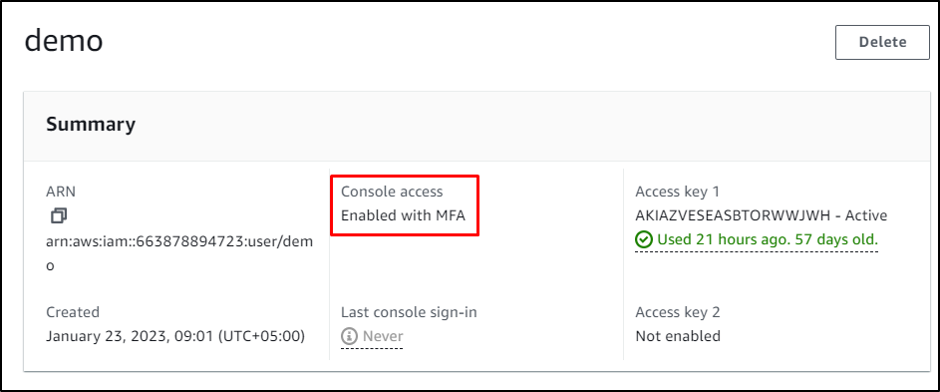
It’s required to have a profile enabled with MFA:
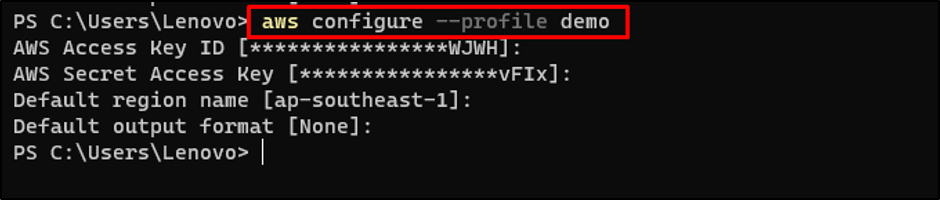
Go to the Terminal out of your native system and configure the AWS CLI:
aws configure –profile demo
Use the AWS CLI command to substantiate configuration:
Working the above command displayed the S3 bucket identify exhibiting that the configuration is right:
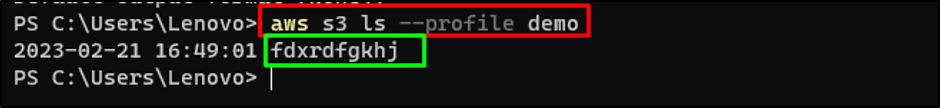
Head again to the IAM Customers web page and click on on the “Permissions” part:
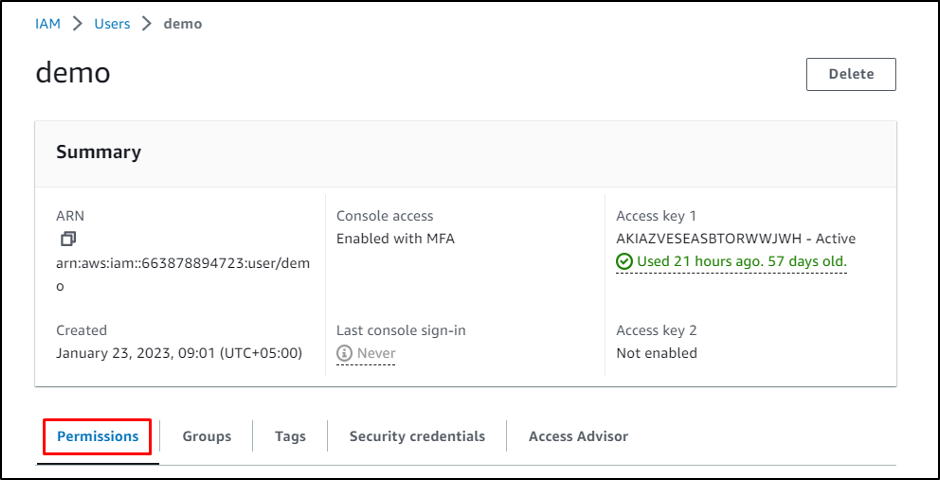
Within the permissions part, develop the “Add permissions” menu and click on on the “Create inline coverage” button:
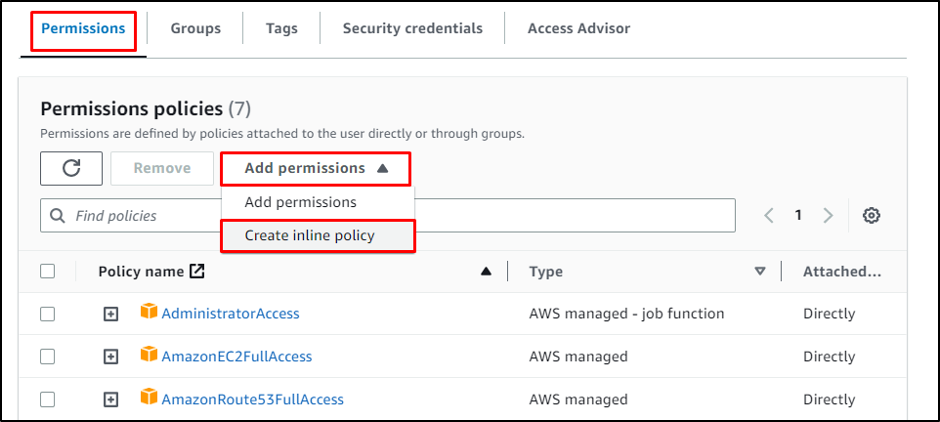
Paste the next code on the JSON part:
“Model”: “2012-10-17”,
“Assertion”: [
{
“Sid”: “MustBeSignedInWithMFA”,
“Effect”: “Deny”,
“NotAction”: [
“iam:CreateVirtualMFADevice”,
“iam:DeleteVirtualMFADevice”,
“iam:ListVirtualMFADevices”,
“iam:EnableMFADevice”,
“iam:ResyncMFADevice”,
“iam:ListAccountAliases”,
“iam:ListUsers”,
“iam:ListSSHPublicKeys”,
“iam:ListAccessKeys”,
“iam:ListServiceSpecificCredentials”,
“iam:ListMFADevices”,
“iam:GetAccountSummary”,
“sts:GetSessionToken”
],
“Useful resource”: “*”,
“Situation”: {
“BoolIfExists”: {
“aws:MultiFactorAuthPresent”: “false”
}
}
}
]
}
Choose the JSON tab and paste the above code contained in the editor. Click on on the “Evaluation coverage” button:
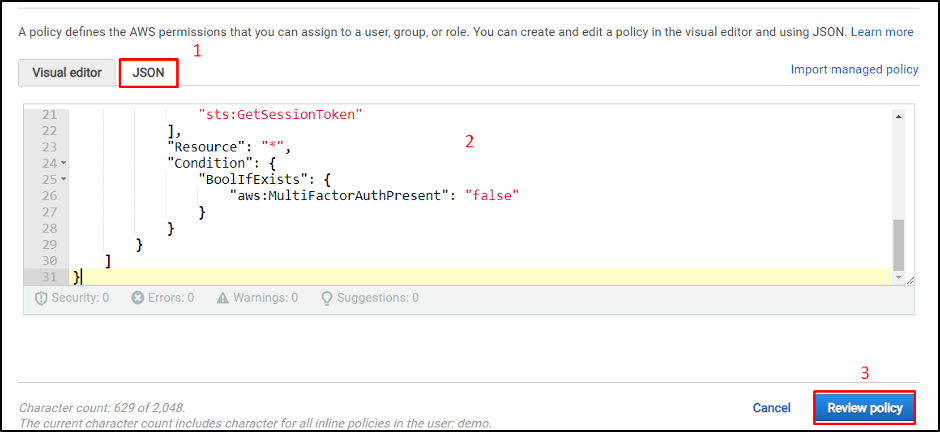
Kind the identify of the coverage:
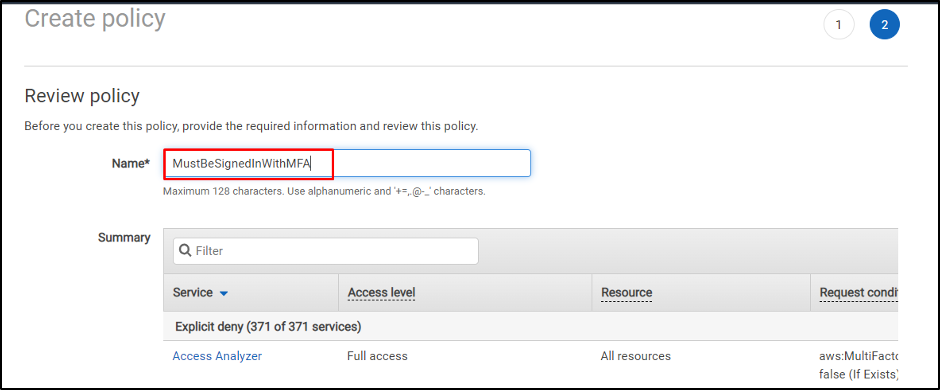
Scroll all the way down to the underside of the web page and click on on the “Create coverage” button:
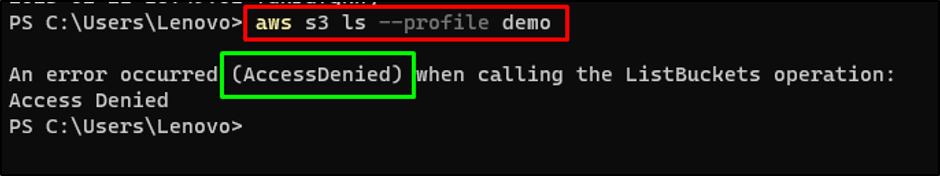
Head again to the terminal and verify once more the AWS CLI command:
Now the execution of the command shows the “AccessDenied” error:
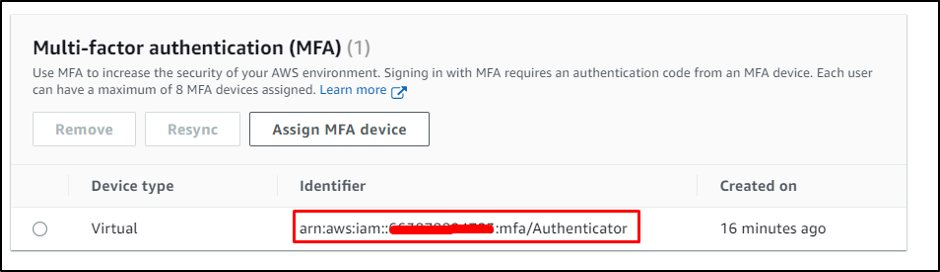
Copy the ARN from the “Customers” MFA account:
The next is the syntax of the command to get the credentials for the MFA account:
aws sts get-session-token –serial-number arn-of-the-mfa-device –token-code code-from-token
Change the “arn-of-the-mfa-device” with the Identifier copied from the AWS IAM dashboard and alter “code-from-token” with the code from the MFA utility:
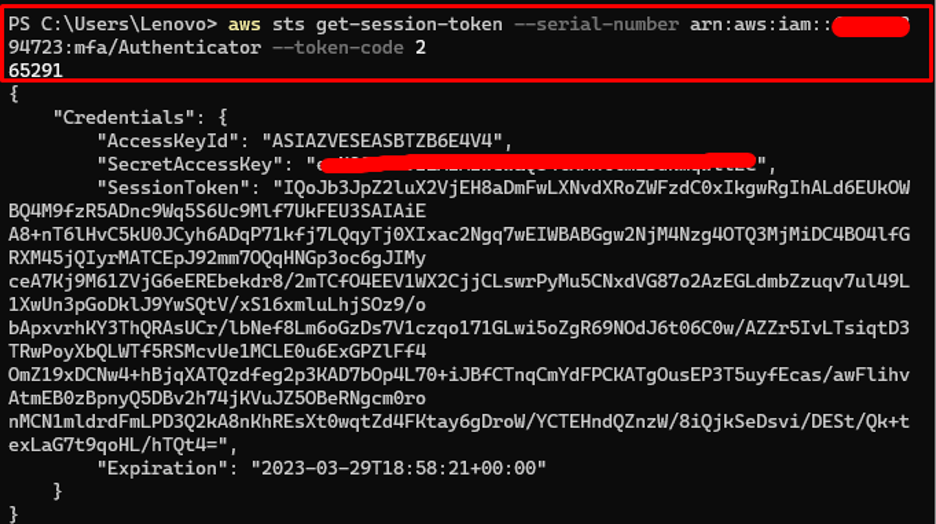
aws sts get-session-token –serial-number arn:aws:iam::*******94723:mfa/Authenticator –token-code 265291
Copy the offered credentials on any editor for use within the credentials file later:
Use the next command to edit the AWS Credentials file:
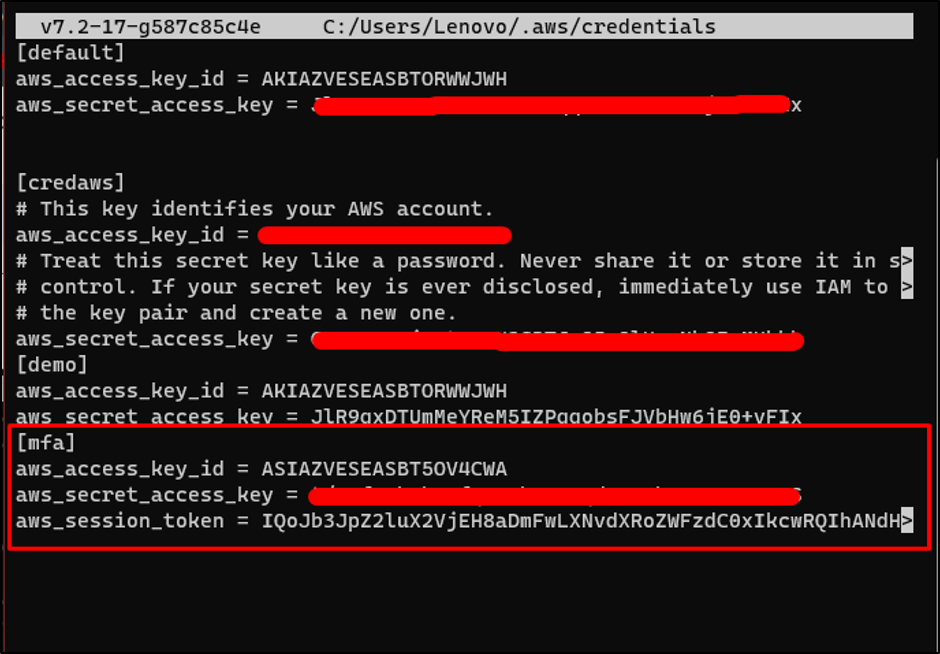
Add the next code to the credentials file:
[mfa]
aws_access_key_id = AccessKey
aws_secret_access_key = SecretKey
aws_session_token = SessionToken
Change the AccessKey, SecretKey, and SessionToken with the “AccessKeyId”, “SecretAccessId”, and “SessionToken” offered within the earlier step:
[mfa]
aws_access_key_id = AccessKey
aws_secret_access_key = t/SecretKey
aws_session_token = IQoJb3JpZ2luX2VjEH8aDmFwLXNvdXRoZWFzdC0xIkcwRQIhANdHKh53PNHamG1aaNFHYH+6x3xBI/oi4dPHi9Gv7wdPAiBFqZZtIcHg+A6J4HqV9pvN1AmCsC+WdBFEdNCtIIpCJirvAQhYEAEaDDY2Mzg3ODg5NDcyMyIM6ujtSkPhFzLfhsW6KswBiBfBeZAaIBPgMuLAKbRym58xlbHoQfAygrxrit671nT+43YZNWpWd/sX/ZpHI56PgBsbc6g2ZfBRQ/FTk3oSjWbl9e/SAzPgPLhje6Cf4iEc8slLjwDs/j5EGymADRowQDJsVvKePy1zTMXUj1U1byb0X6J3eNEPvx24Njg4ugJ95KzpPGnqdLrp/z/BnSN3dMt77O2mAleniQyPpw/nVGn73D60HtBx3EJzvmvwthHcdA6wM/Gvdij0VcRC4qoN/8FaymyCwvwvMeAVMPu/j6EGOpgBK4sd1Ek++dSVSCWBeOX6F93SgnTZkjKWFkc6ki4QXP0IQm/+NvBGviMJQAyJ/yRU58tW9Q9ERhgHSfwZNSKQ3EWsPlaCitJqQV15l8VDtPEyNgl1exAzBSt2ZZBthUc3VHKN/UyhgUXtn8Efv5E8HP+fblbeX2ExlfC9KnQj6Ob5sP5ZHvEnDkwSCJ6wpFq3qiWR3n75Dp0=
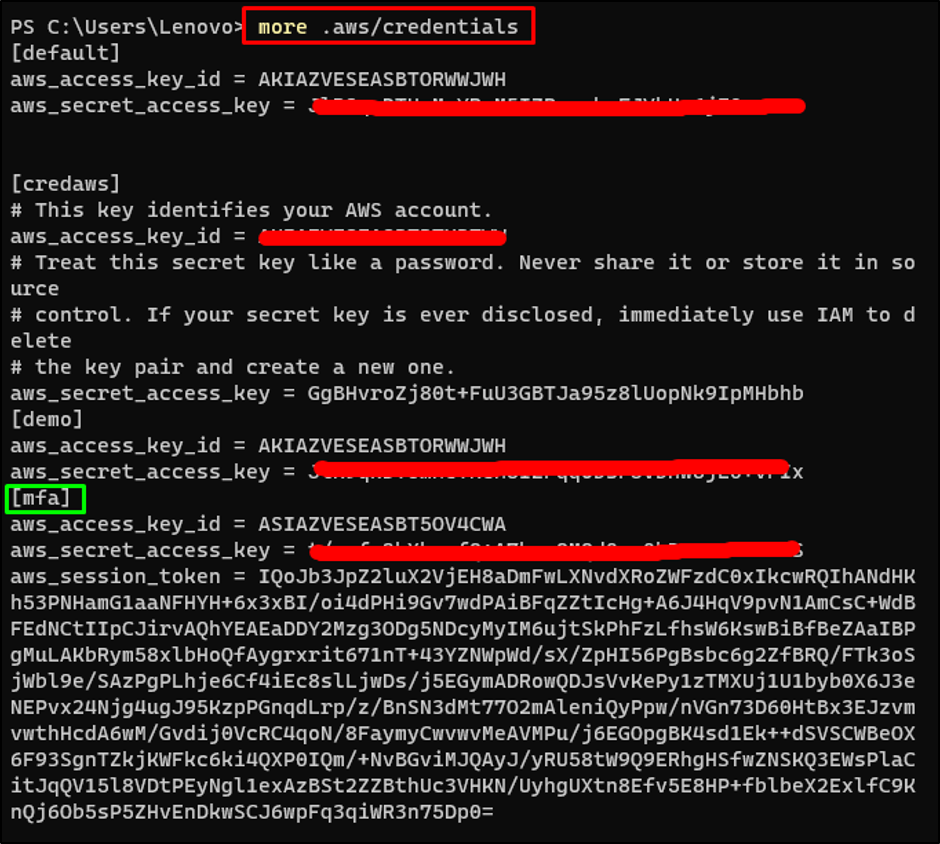
Examine the added credentials utilizing the next command:
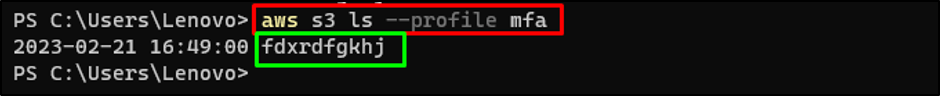
Use the AWS CLI command with the “mfa” profile:
Efficiently working the above command means that the MFA profile has been added efficiently:
That is all about utilizing MFA with AWS CLI.
Conclusion
To make use of MFA with AWS CLI, assign MFA to the IAM consumer after which configure it on the terminal. After that, add an inline coverage to the consumer so it will possibly solely use sure instructions via that profile. As soon as that’s completed, get MFA credentials after which replace them on the AWS credentials file. Once more, use AWS CLI instructions with an MFA profile to handle AWS assets. This information has defined methods to use MFA with AWS CLI.
