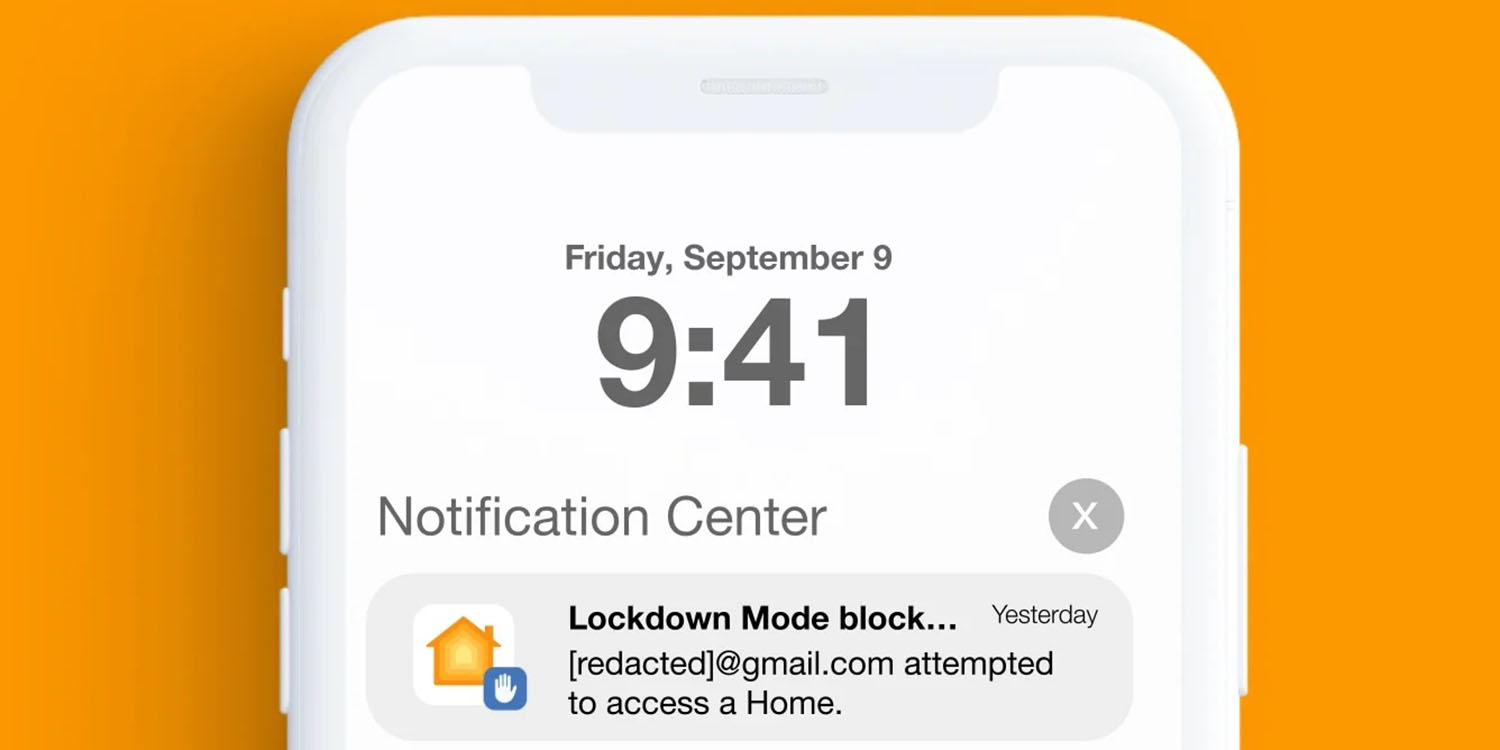
An NSO zero-click iPhone hack labored by getting access to HomeKit on the machine, nevertheless it was blocked by these utilizing Apple’s Lockdown Mode safety function, with the telephone alerting them to the entry try.
Nonetheless, two different NSO zero-click assaults seemingly succeeded – each exploiting vulnerabilities within the Discover My app …
Zero-click assaults
Most assaults on units depend on tricking house owners into putting in malware by tapping a hyperlink. A typical tactic is to ship a message that seems to be from Apple, PayPal, or related.
Tech-savvy and security-conscious iPhone customers know the indicators of this, however there has lengthy been no safety in opposition to so-called zero-click assaults. With these, a tool might be compromised with out the person doing something in any respect.
Adware firm NSO has been infamous for utilizing zero-click assaults on iPhones, a lot of which had been utilized by governments with poor human rights information to spy on political opponents, journalists, legal professionals, and human rights activists. In these, merely receiving an iMessage – with out even opening it – is sufficient to give distant entry to your iPhone.
Lockdown Mode
To guard these almost certainly to be focused by state-sponsored assaults, Apple final yr launched Lockdown Mode – a approach of limiting the performance of an iPhone in methods designed to attenuate the danger of a zero-click assault working.
Lockdown Mode is simply meant for use by those that contemplate themselves to be at severe danger of presidency surveillance. It drastically reduces the function set of an iPhone, together with blocking most message attachments, disabling many web sites, and so forth.
Three new NSO zero-click iPhone hacks detected
Safety researchers at Citizen Lab have launched particulars of three new NSO zero-click iPhone hacks. They had been detected late final yr, however the firm withheld particulars till Apple was in a position to patch iOS to dam the assaults.
The assault vector utilized by two of the three assaults seems to be to ship an iMessage containing malware, which then exploits vulnerabilities in different inventory Apple apps.
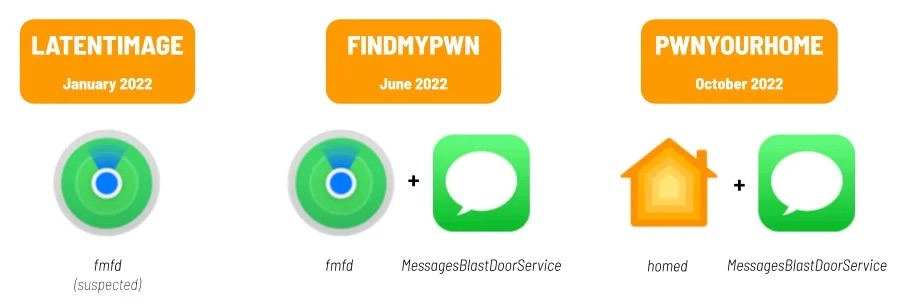
“PWNYOURHOME,” was deployed in opposition to iOS 15 and iOS 16 beginning in October 2022. It seems to be a novel two-step zero-click exploit, with every step focusing on a special course of on the iPhone. Step one targets HomeKit, and the second step targets iMessage.
“FINDMYPWN” was deployed in opposition to iOS 15 starting in June 2022. It additionally seems to be a two-step exploit; step one targets the iPhone’s Discover My function, and the second step targets iMessage.
We shared forensic artifacts with Apple in October 2022, and extra forensic artifacts relating to PWNYOURHOME in January 2023, main Apple to launch a number of safety enhancements to HomeKit in iOS 16.3.1
As soon as we had recognized FINDMYPWN and PWNYOURHOME, we found traces of NSO Group’s first 2022 zero-click (“LATENTIMAGE”) on a single goal’s telephone. This exploit may have concerned the iPhone’s Discover My function, however is a special exploit chain than FINDMYPWN.
The report says that targets who had Lockdown Mode activated had been alerted to one in all these assaults.
For a short interval, targets that had enabled iOS 16’s Lockdown Mode function obtained real-time warnings when PWNYOURHOME exploitation was tried in opposition to their units. Though NSO Group could have later devised a workaround for this real-time warning, we’ve got not seen PWNYOURHOME efficiently used in opposition to any units on which Lockdown Mode is enabled.
It stated that the assaults had been used in opposition to human rights teams in Mexico. The United Nations reported final yr that greater than 100,000 folks in Mexico have been registered as “disappeared,” and presumed to have been killed by a authorities with an extended historical past of political opponents vanishing with out hint.
FTC: We use revenue incomes auto affiliate hyperlinks. Extra.


