MimiPenguin is a free and open supply, easy but highly effective Shell/Python script used to dump the login credentials (usernames and passwords) from the present Linux desktop person and it has been examined on numerous Linux distributions.
Moreover, it helps functions similar to VSFTPd (lively FTP shopper connections), Apache2 (lively/outdated HTTP BASIC AUTH periods however this requires Gcore), and OpenSSH-server (lively SSH connections with sudo command utilization).
Importantly, it’s progressively being ported to quite a few languages to help all conceivable post-exploit conditions.
How Does MimiPenguin Work?
To know how MimiPenguin works, it’s essential to remember that all if not most Linux distributions retailer a substantial amount of such vital info as credentials, encryption keys, in addition to private knowledge in reminiscence.
Notably usernames and passwords are held by processes (operating applications) in reminiscence and saved as plain textual content for comparatively lengthy intervals of time.
MimiPenguin technically exploits these clear-text credentials in reminiscence – it dumps a course of and extracts strains which have a probability of accommodating clear-text credentials.
It then tries to carry out a calculation of every phrase’s probabilities of being current by figuring out hashes in /and so on/shadow, reminiscence, and regex searches. As soon as it finds any, it prints them on customary output.
Putting in MimiPenguin in Linux Techniques
We’ll use git to clone the MimiPenguin repository, so first set up git on the system if in case you don’t have it.
$ sudo apt set up git [On Debian, Ubuntu and Mint] $ sudo yum set up git [On RHEL/CentOS/Fedora and Rocky/AlmaLinux] $ sudo emerge -a git [On Gentoo Linux] $ sudo apk add git [On Alpine Linux] $ sudo pacman -S git [On Arch Linux] $ sudo zypper set up git [On OpenSUSE]
Then clone the MimiPenguin listing in your house folder (wherever else) as proven.
$ git clone https://github.com/huntergregal/mimipenguin.git
View Linux Person Passwords
After getting downloaded the listing, transfer into it and run mimipenguin as follows:
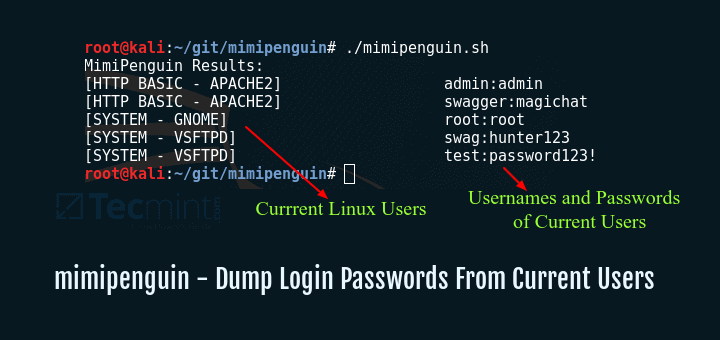
$ cd mimipenguin/ $ ./mimipenguin.sh
Word: Should you encounter the error beneath, use the sudo command like so:
Root required - You're dumping reminiscence... Even mimikatz requires an administrator
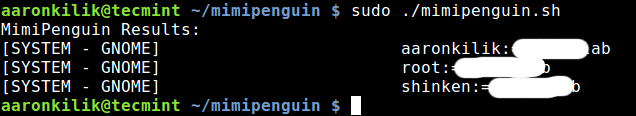
From the output above, mimipenguin gives you with the desktop atmosphere together with the username and password.
Alternatively, run the Python script as follows:
$ sudo ./mimipenguin.py
Word that generally gcore could grasp the script (this can be a identified downside with gcore).
Future Updates
Beneath is an inventory of options but to be added to mimipenguin:
- Bettering total effectiveness
- Including extra help and different credential places
- Together with help for non-desktop environments
- Including help for LDAP
Do share any extra concepts referring to the mimipenguin software or problems with cleartext credentials in reminiscence in Linux through the remark part beneath.
If You Admire What We Do Right here On TecMint, You Ought to Contemplate:
TecMint is the quickest rising and most trusted group web site for any type of Linux Articles, Guides and Books on the net. Hundreds of thousands of individuals go to TecMint! to go looking or browse the 1000’s of revealed articles accessible FREELY to all.
Should you like what you’re studying, please contemplate shopping for us a espresso ( or 2 ) as a token of appreciation.
We’re grateful in your by no means ending help.