
Yesterday noticed @analyst941 delete his Twitter account, claiming that he had been pressured to take action after Apple carried out a “multi-step sting” operation. Whether or not that is true, or only a face-saving story for getting issues flawed, it’s broadly in step with what we find out about how Apple catches leakers.
Apple has so many strategies of figuring out leakers – a few of them extremely refined – that we and others should be extraordinarily cautious as a way to defend our sources …
Apple’s secrecy tradition
With most tech firms, secrecy is a strategy to cease opponents beating them to the punch. In the event that they know or suspect different firms are engaged on the identical thought, they need to be first to market, so don’t need anybody else to search out out their plans, or how shut they’re to launching.
With Apple, nonetheless, the corporate’s major motivation is completely different. The corporate hardly ever goals to be first to market; as an alternative, it watches and waits whereas different firms rush merchandise out of the door, and figures out how you can enhance on their choices. Apple goals to be greatest, not first.
Nevertheless it does nonetheless need to defend its future plans, and that’s as a result of a realisation Steve Jobs had: that there’s magic to a sudden reveal. The launch of the unique iPhone is probably the most well-known instance.
Immediately we’re introducing three revolutionary merchandise of this class. The primary one is a widescreen iPod with contact controls. The second is a revolutionary cell phone. And the third is a breakthrough Web communications system.
The reveal, after all, was that they had been all the identical system.
It’s this need for the magic of shock which varieties the primary driver for Apple’s tradition of secrecy.
How Apple protects its secrets and techniques
The Cupertino firm has some ways of defending its secrets and techniques.
For instance, it has a silo system for product growth. People, or small groups, shall be working in isolation on one aspect of a product, whereas different groups – whose existence isn’t even identified to one another – shall be engaged on different parts. Product builders aren’t allowed to share their work, even with different Apple workers (one of many causes that the well-known Apple Park round design to encourage collaboration is extra PR picture than actuality).
In some instances, workers don’t even know what product class they’re engaged on. For instance, they could be engaged on audio tech with out even figuring out whether or not will probably be utilized in a HomePod, a Mac, AirPods, or iPhone audio system.
Prototype gadgets are very fastidiously disguised in the event that they should be utilized in public, with nice care taken to log and observe them – a lesson Apple discovered the laborious means, after the notorious iPhone 4 prototype bar incident!
IT techniques will after all be fastidiously protected, Apple monitoring each community exercise and use of issues like USB keys.
Apple additionally warns workers that leaking data is a fireable offence – and that the corporate could even go after them for monetary damages.
All the identical, some workers do leak data, and even with a silo system, there shall be some Apple secrets and techniques identified to a major variety of individuals. When data is leaked, the corporate wants some strategy to determine who leaked it, and it has some fairly sneaky methods to take action! These are only a few solutions to the query of how Apple catches leakers …

How Apple catches leakers
Given Apple’s emphasis on product design, it’s no shock that the corporate works notably laborious to forestall leaks of visible supplies: product photos, drawings, blueprints, CAD photos, and the like.
It was commonplace for tech websites to share these photos straight, however Apple got here up with all kinds of the way to determine precisely which copy of a picture was shared. Every particular person who obtained a picture can be given a novel one.
Listed below are only a few of the strategies Apple is thought or believed to make use of …
Invisible watermarks
We’re all accustomed to seen watermarks utilized by websites corresponding to ourselves, to make sure that authentic photos are correctly credited, but it surely’s additionally doable to embed watermarks that are invisible to the bare eye, however will be digitally detected.
For instance, this sq. seems to be all black:
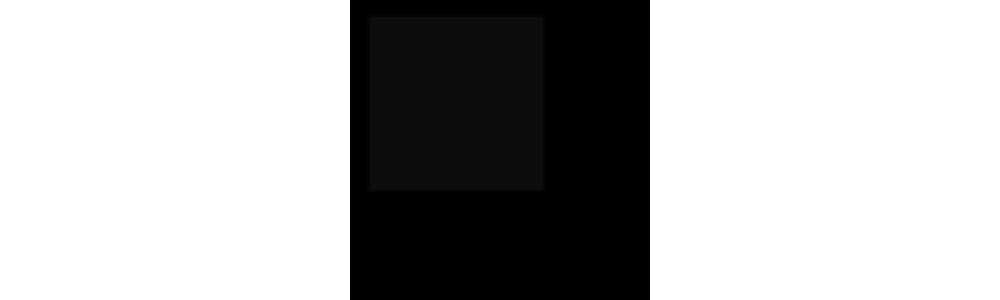
The truth is, one part of it’s #0D0D0D as an alternative of #000000. By making adjustments as refined as this to completely different pixels, you possibly can create a near-infinite variety of variations, every of which might be inconceivable to differentiate by eye.
We’ve used black for instance, however the identical can after all be finished with actually any colour in a picture.
That is the rationale why we by no means share precise photos equipped by our sources. We at all times recreate them, and by no means precisely.
Filenames
Another excuse by no means to make use of authentic photos is that it’s very simple for Apple to make use of distinctive filenames, for instance:
- very_secret_image_46793459583203.jpg
- very_secret_image_46793469583203.jpg
Serial numbers
Doc serial numbers is one other variation. For instance, when Apple shares movies with workers, every is watermarked with an ID quantity which is probably going cross-referenced with the Apple Join ID of the member of employees.
Refined typeface adjustments
Many photos include textual content, and refined typeface adjustments are one simple strategy to create distinctive variations. For instance, with a serif font, a model might be created with a single pixel lacking from a single stroke of a single occasion of a single letter. Font sizes will also be scaled up or down by as little as one pixel.
Non-subtle typeface adjustments
Generally, Apple makes use of the other strategy, and chooses very unrefined adjustments. If it desires workers to be very conscious that their copy is exclusive, it has used issues like random italics or daring. For instance:
This yr, the iPhone 15 will launch on Tuesday August 29 as an alternative of the standard September timing.
That is an strategy we’ve seen Apple take with paperwork despatched to retailer employees forward of product launches, as a way to make it painfully clear that the corporate is watching. Despite the fact that an worker could retype one thing, fairly than copying and pasting, it’ll make them concern different figuring out options, corresponding to …
Wording or punctuation adjustments
Tiny adjustments in wording are trickier in the event you’re making an attempt to offer a novel copy to lots of people, however will be very useful when you’ve narrowed it right down to a handful of individuals. For instance:
This yr, the iPhone 15 will launch on Tuesday August 29 as an alternative of the standard September timing.
versus:
This yr, the iPhone 15 shall be launched on Tuesday August 29 as an alternative of the standard September timing.
versus:
This yr, the iPhone 15 will launch on Tuesday August 29, as an alternative of the standard September timing.
The addition or removing of one thing as refined as a comma will be sufficient.
Once more, we are going to paraphrase to keep away from this lure.
False data
A easy strategy with issues like specs is to have a tiny change of element in every copy of the doc. This might, clearly, should be to a component the worker involved isn’t engaged on.
For instance, for an worker whose work doesn’t relate to radio bands, think about how simple it will be to vary a single digit on this:

Or for one engaged on radio bands, altering f/1.78 to f/1.76 on this:
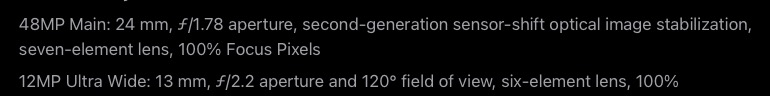
Faux dates, costs, colours, and extra are doable.
When it comes to how Apple catches leakers, these are simply among the methods we all know or suspect the corporate makes use of.
Is @analyst941’s declare true?
It’s inconceivable to say. The closest we’re ever more likely to come to figuring out is seeing what number of of their different claims are true – however even then, if it was certainly a multi-step narrowing-down course of, we don’t know at what level Apple began feeding false data to the sister.
I stated at the start that their declare is broadly in step with techniques utilized by Apple. Nevertheless, on this case the pretend data was that Remaining Lower Professional was scheduled for a launch on iPad in 2024, adopted by Logic Professional in 2025 – when the fact is that each can be launched simply days later.
That’s a huge distinction between actual and faux data, when a a lot subtler distinction would have achieved the identical factor. Apple may, for instance, have seeded the data that FCP can be launched in June, and Logic Professional in July. It could have been a lot more durable for an worker to know {that a} smaller distinction was false.
So personally, whereas the tactic is a identified one, I’m a bit skeptical on this specific case.
Pictures: Decide Lasers/Unsplash and Emiliano Vittoriosi/Unsplash
FTC: We use revenue incomes auto affiliate hyperlinks. Extra.


