In Unix/Linux techniques, the root person account is the tremendous person account, and it could subsequently be used to do something and the whole lot achievable on the system.
Nevertheless, this may be very harmful in so some ways – one might be that the root person may enter a incorrect command and breaks the entire system or an attacker will get entry to a root person account and takes management of the entire system and who is aware of what he/she will presumably do.
Based mostly upon this background, in Ubuntu and Ubuntu derivatives, the root person account is locked by default, common customers (system directors or not) can solely achieve superuser privileges by utilizing the sudo command.
And one of many worst issues that may occur to a Ubuntu System admin is shedding privileges to make use of the sudo command, a state of affairs generally known as “damaged sudo”. This may be completely devastating.
A damaged sudo could also be attributable to any of the next:
- A person shouldn’t have been faraway from the sudo or admin group.
- The /and many others/sudoers file was altered to stop customers within the sudo or admin group from elevating their privileges to that of root utilizing the sudo command.
- The permission on /and many others/sudoers file shouldn’t be set to 0440.
With a purpose to carry out essential duties in your system comparable to viewing or altering necessary system information, or updating the system, you want the sudo command to achieve superuser privileges. What if you’re denied utilization of sudo resulting from a number of of the explanations we talked about above.
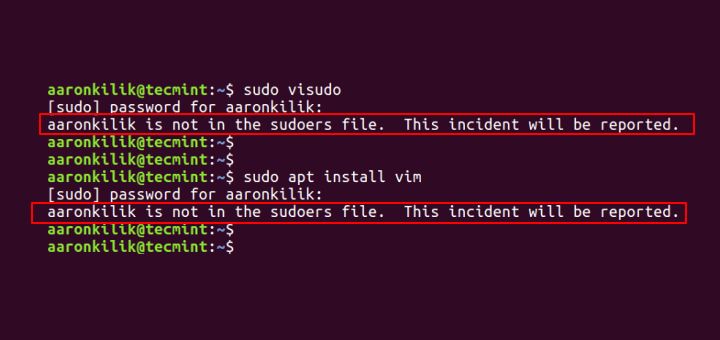
Under is a picture displaying a case wherein the default system person is being prevented from operating the sudo command:
[email protected] ~ $ sudo visudo [ sudo ] password for aaronkilik: aaronkilik shouldn't be within the sudoers file. This incident shall be reported. [email protected] ~ $ sudo apt set up vim [ sudo ] password for aaronkilik: aaronkilik shouldn't be within the sudoers file. This incident shall be reported.
How To Repair Damaged sudo Command in Ubuntu
When you occur to be operating solely Ubuntu in your machine, after powering it, press the Shift key for a couple of seconds to get the Grub boot menu. However, if you’re operating a dual-boot (Ubuntu alongside Home windows or Mac OS X), then it’s best to see the Grub boot menu by default.
Utilizing the Down Arrow, choose “Superior choices for Ubuntu” and press Enter.
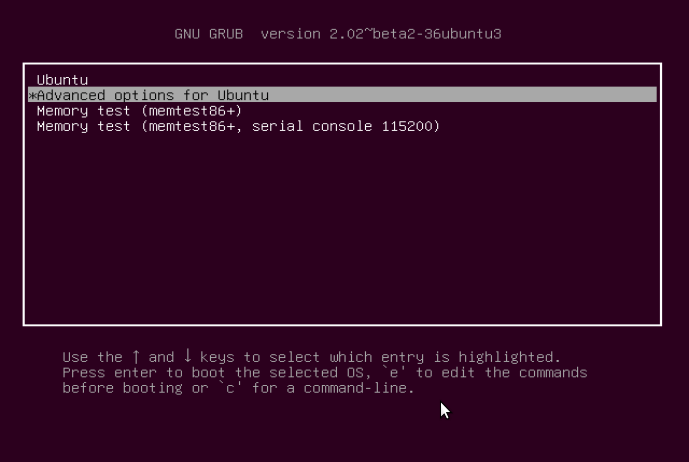
You can be on the interface under, choose the kernel with the “restoration mode” possibility as under and press Enter to advance to the “Restoration menu”.
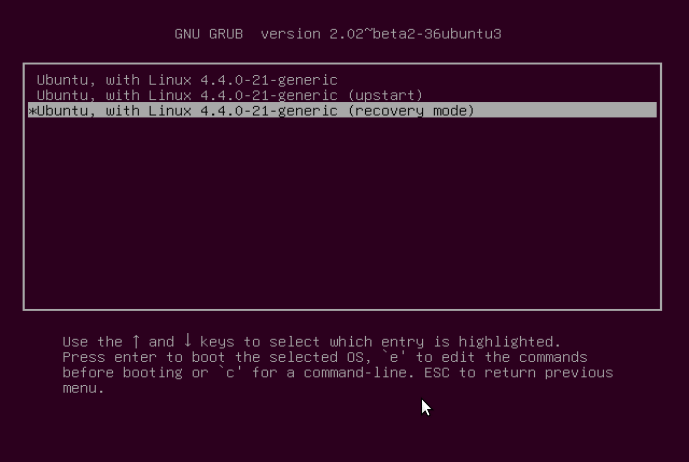
Under is the “Restoration menu”, indicating that the foundation filesystem is mounted as read-only. Transfer over to the road “root Drop to root shell immediate”, then hit Enter.
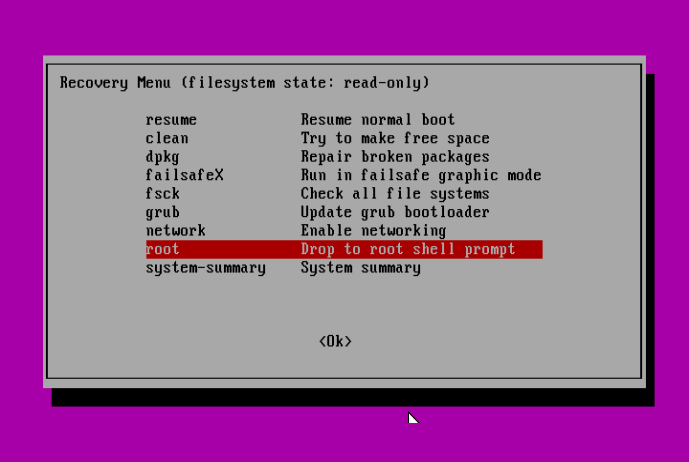
Subsequent, press Enter for upkeep:
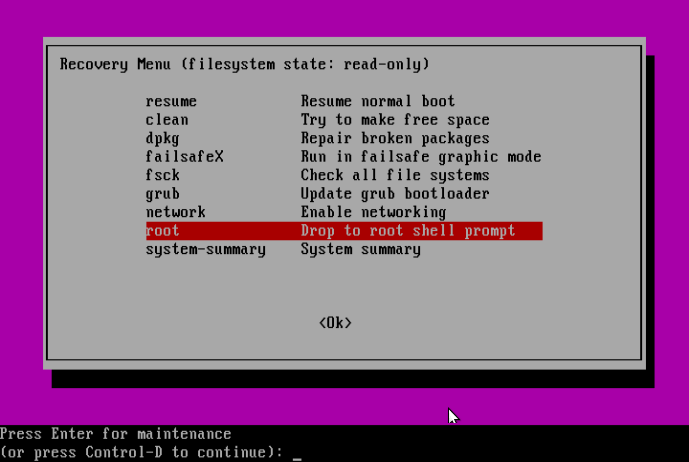
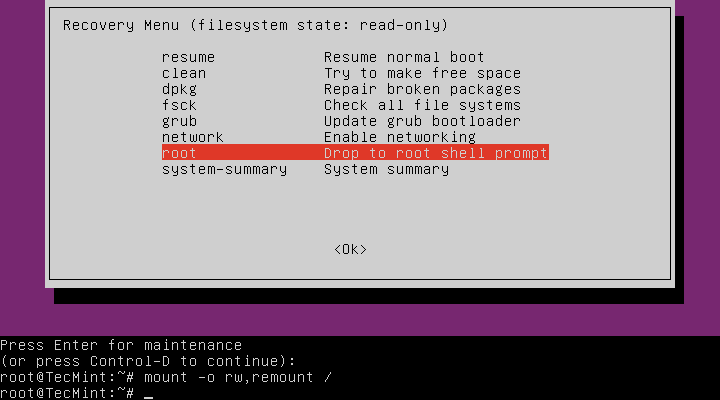
At this level, you ought to be on the root shell immediate. As we had seen earlier than, the filesystem is mounted as read-only, subsequently, to make modifications to the system we have to remount is as learn/write by operating the command under:
# mount -o rw,remount /
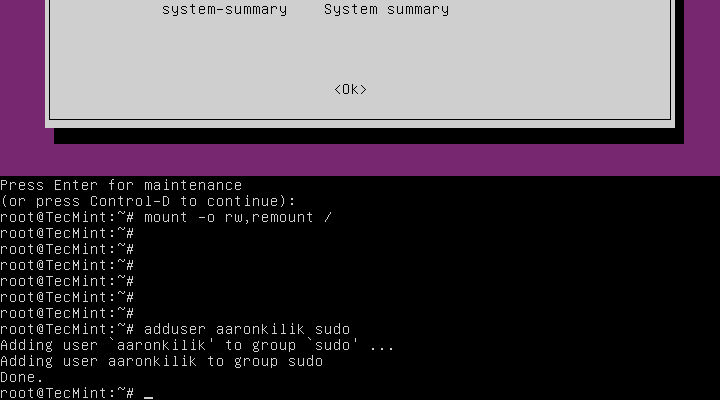
Fixing Case #1 – Add Person to sudo or admin Group
Assuming {that a} person has been faraway from the sudo group, so as to add the person again to the sudo group concern the command under:
# adduser username sudo
Observe: Bear in mind to make use of the precise username on the system, in my case, it’s aaronkilik.
Or else, beneath the situation {that a} person has been faraway from the admin group, run the next command:
# adduser username admin
Fixing Case #2 – Granting sudo Privileges to Customers
On the belief that the /and many others/sudoers file was altered to stop customers within the sudo or admin group from elevating their privileges to that of a brilliant person, then make a backup of the sudoers information as follows:
# cp /and many others/sudoers /and many others/sudoers.orginal
Subsequently, open the sudoers file.
# visudo
and add the content material under:
# # This file MUST be edited with the 'visudo' command as root. # # Please contemplate including native content material in /and many others/sudoers.d/ as an alternative of # instantly modifying this file. # # See the person web page for particulars on write a sudoers file. # Defaults env_reset Defaults mail_badpass Defaults secure_path="/usr/native/sbin:/usr/native/bin:/usr/sbi$ # Host alias specification # Person alias specification # Cmnd alias specification # Person privilege specification root ALL=(ALL:ALL) ALL # Members of the admin group could achieve root privileges %admin ALL=(ALL) ALL # Permit members of group sudo to execute any command %sudo ALL=(ALL:ALL) ALL # See sudoers(5) for extra data on "#embody" directives: #includedir /and many others/sudoers.d
Fixing Case #3 – Setting Right Permission on sudoers File
Supposing that the permission on the /and many others/sudoers file shouldn’t be set to 0440, then run the next command to make it proper:
# chmod 0440 /and many others/sudoers
Final however not least, after operating all the mandatory instructions, kind the exit command to return to the “Restoration menu”:
# exit
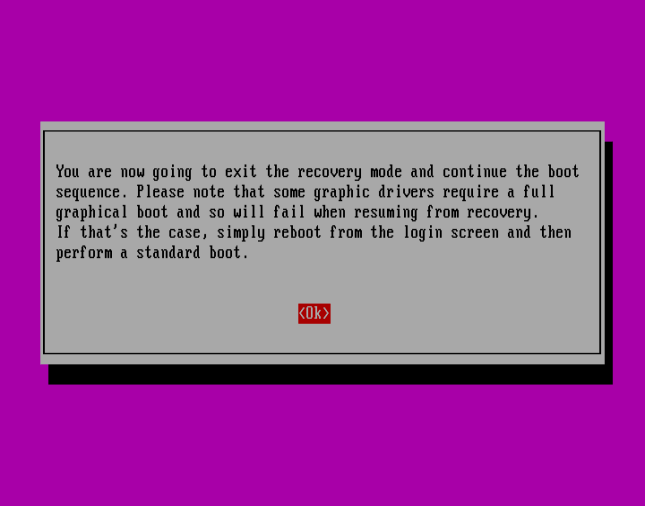
Use the Proper Arrow to pick out <Okay> and hit Enter:
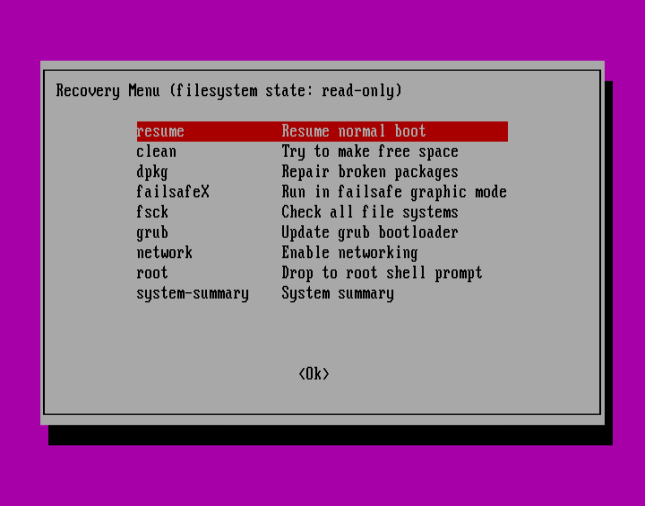
Press <Okay> to proceed with regular boot sequence:
Abstract
This methodology ought to work simply advantageous particularly when it’s an administrative person account concerned, the place there is no such thing as a different possibility however to make use of the restoration mode.
Nevertheless, if it fails to give you the results you want, attempt to get again to us by expressing your expertise through the suggestions part under. You possibly can as properly supply any recommendations or different potential methods to unravel the problem at hand or enhance this information altogether.