AppArmor is a Linux software program safety mechanism that may be very efficient and user-friendly. AppArmor is a core enchancment that restricts the applications to particular sources. It connects the entry management properties to the applications as a substitute of customers. AppArmor secures the Linux working system and apps from quite a few assaults by implementing the safety insurance policies which is often known as an AppArmor profile. The AppArmor profile includes easy textual content information. When defining the file entry, each file globbing and absolute paths may be utilized.
We’ve got two useful modes of AppArmor implement and complain. The AppArmor manufacturing standing is in enforced mode by default, however the complain mode is helpful for logging violations and defining a rule set primarily based on precise operation patterns. In distinction, to being a part of the framework, AppArmor is an add-on characteristic that may be added, modified, disabled, or uninstalled. We are going to discover the implementation of AppArmor on this tutorial to get extra particulars about it.
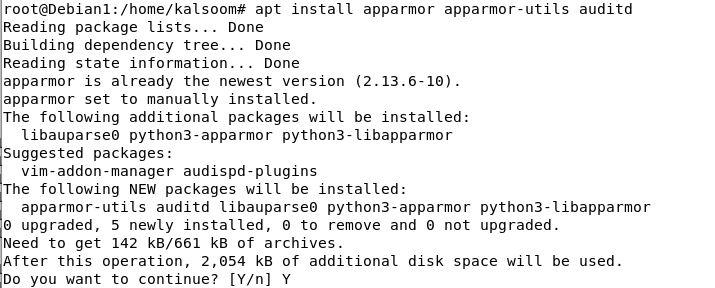
Set up of AppArmor in Debian
AppArmor is already arrange and loaded within the Debian working system. It leverages the profiles of the appliance which is required by this system to find out the information and permissions. Some utilities set up their profiles, whereas the AppArmor-profiles package deal accommodates extra profiles. The apt command is used to put in the “audit” apparmor-utils within the Debian working system which is proven within the following picture. We will take away the “audit” utils from the command if we don’t require the instruments to create the profiles. Observe that we run this command as a root.
Enabling the AppArmor in Debian
Now, the AppArmor utility to generate a profile is put in. We allow the AppArmor Linux Safety Modules from the Linux kernel command line. We observe the next given steps to allow the AppArmor within the Debian working system:
Step 1: Create the listing.
mkdir -p /and so on/default/grub.d
Step 2: Generate the “ /and so on/default/grub.d/apparmor.cfg” file and save the content material that we echo within the following:
| sudo tee /and so on/default/grub.d/apparmor.cfg
Step 3: Replace the “grub” below the privilege of sudo command.
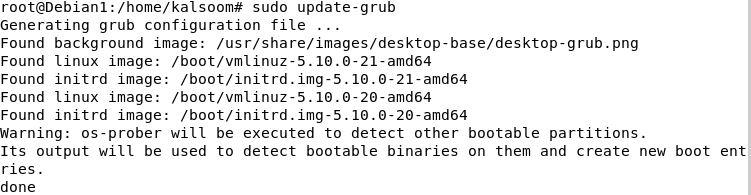
Step 4: Reboot the Debian working system. As soon as the reboot is completed, we will verify if the standing of AppArmor is enabled or not by executing the next command. It returns “Y” which signifies “Sure” as a result of the AppArmor is enabled inside the Debian system:
cat /sys/module/apparmor/parameters/enabled
![]()
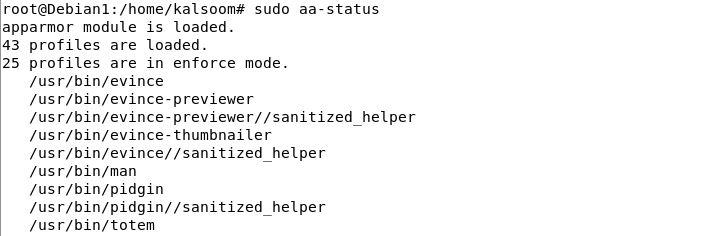
Step 5: Use the command to get the present standing of every AppArmor profile that’s loaded for functions and processes. We will see the mode compliance of every profile which is loaded within the following illustration. The output shows that “43” profiles are loaded as AppArmor profiles and the “25” profiles of AppArmor are in implement mode by default. There exist two modes of the AppArmor profiles – some are in implement mode and a few are in complain mode. We will modify the execution mode for every profile that’s outlined.
Modifying the AppArmor Profile in Debian
As we talked about earlier, the modes may be switched from the required modes of the AppArmor profile. Which means the implement mode may be modified with the complain mode and vice versa. We’ve got an AppArmor profile as “dhclient” which is in an enforced mode. The complain mode may be accessed by operating the next command. The output shows the message of setting the dhclient in complain mode:
sudo aa-complain /sbin/dhclient
![]()
To change the complain mode in an implement mode once more, now we have a command to attain this. The command makes use of the “implement” key phrase with the dhclient profile.
sudo aa-enforce /sbin/dhclient
![]()
Moreover, the execution mode configuration path is /and so on/apparmor.d/* for all of the AppArmor profiles. We will set the execution mode of all of the AppArmor profiles in complain mode by making use of the next sudo command within the terminal:
sudo aa-complain /and so on/apparmor.d/*
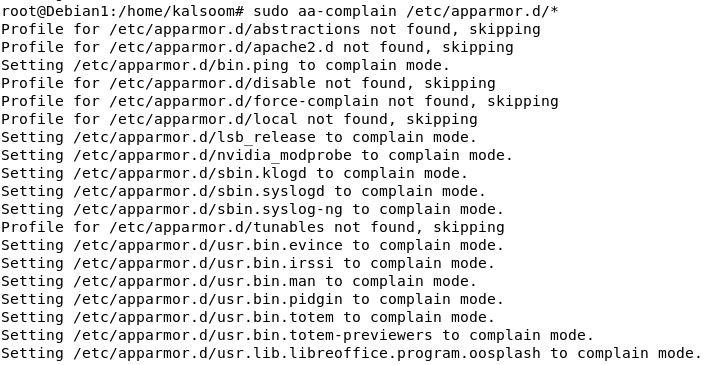
We will additionally set the trail of the execution mode for all of the profiles of AppArmor to the implement mode utilizing the next command:
sudo aa-enforce /and so on/apparmor.d/*
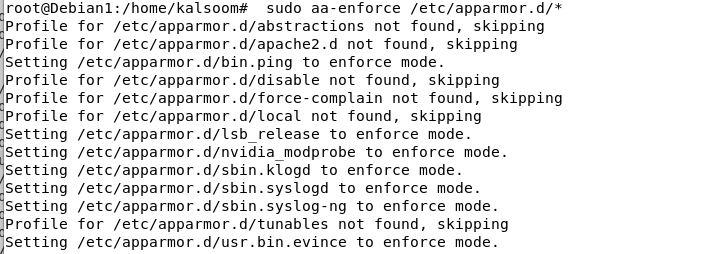
Making a New AppArmor Profile in Debian
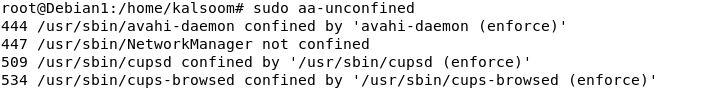
To ascertain a brand new profile, we should decide the functions that require safety however are usually not affiliated with some other AppArmor profile. There are a number of instructions to assemble the AppArmor profiles. However we use the “aa-confined” command to record the profiles that are unconfined. The output signifies that one course of is unconfined to any profiles, whereas the opposite three processes are confined by three profiles in enforced mode by default.
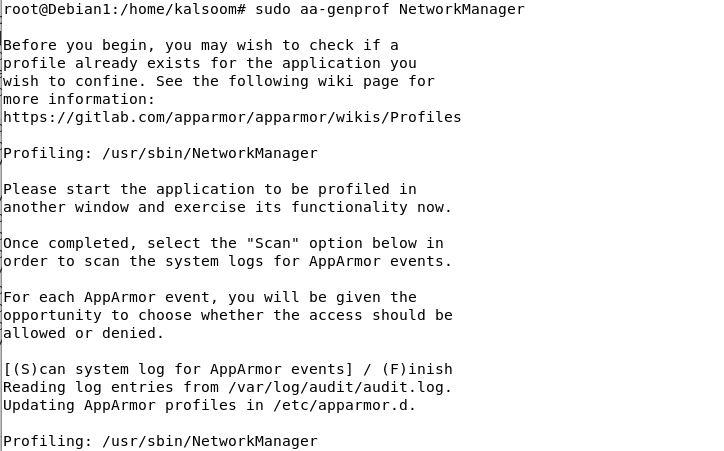
Now, we create the “NetworkManager” AppArmor profile which isn’t confined. For this, we make the most of the “aa-genprof” command and specify the identify of the unconfined profile with it. The generated profile is empty within the enforced mode by default. By urgent the “F”, the creation means of the profile is ended.
sudo aa-genprof NetworkManager
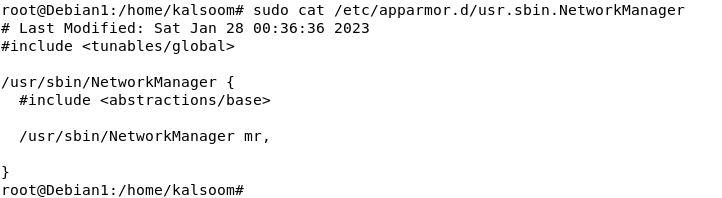
We will change their contents by modifying the next file as there aren’t any such outlined limitations for this profile which units the constraints for this system. The “NetworkManager” profile is now up to date as proven within the Debian terminal:
sudo cat /and so on/apparmor.d/usr.sbin.NetworkManager
Reloading the AppArmor Profiles in Debian
The AppArmor profiles which we beforehand created and modified must be reloaded. To reload each lively AppArmor profile, carry out the next command:
sudo systemctl reload apparmor.service
Subsequent, utilizing the given command, the loaded profiles of AppArmor may be seen. We will see that the created NetworkManager profile is talked about within the output with the enforced mode.
sudo cat /sys/kernel/safety/apparmor/profiles
![]()
Disabling the AppArmor in Debian
The AppArmor utility will not be allowed to be disabled as a result of it’s a safety characteristic. If we disable or take away the AppArmor from our system, now we have to observe these instructions. First, we cease the AppArmor companies utilizing the systemctl:
sudo systemctl cease apparmor
After that, we use one other command which disables the AppArmor from operating when the system boots:
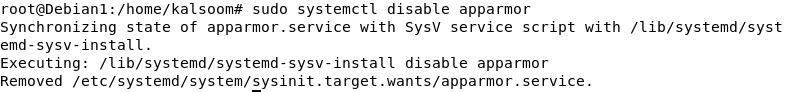
sudo systemctl disable apparmor
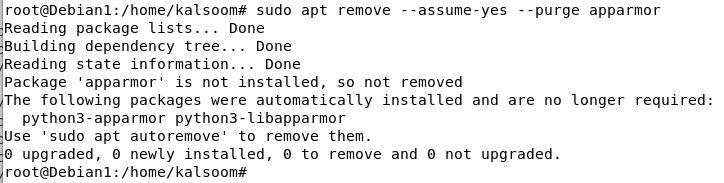
The following executed command makes use of the apt to take away the AppArmor package deal and dependencies from the system.
sudo apt take away –assume-yes –purge apparmor
Conclusion
On this Debian AppArmor article, we explored the methods to work with the AppArmor profiles. We realized the set up command for the AppArmor profiles. After the set up, we enabled the AppArmor inside the Debian system. Then, we modified the modes of present profiles of the AppArmor. We additionally generated a brand new profile that isn’t confined to the AppArmor profiles. The AppArmor may also be disabled or faraway from the system utilizing the precise disabling instructions that are executed within the final a part of this tutorial.
