When the darkish internet is talked about on-line, it’s normally in reference to unlawful markets and arrests made by police.
Certainly, while you’re on the lookout for a solution to a query like, “what’s the darkish internet?” you probably discover out that it’s part of the web the place you should purchase bank card numbers, all types of medicine, weapons, pretend cash, hacked Netflix accounts, stolen subscription credentials, and rather more.
Nonetheless, the darkish internet additionally has a professional aspect. For instance, a few of our favourite social media platforms, like Twitter and Fb, have arrange mirror websites on the darkish internet for individuals who don’t wish to be watched by the federal government. Some customers on the lookout for how you can entry the darkish internet can do that just because they wish to test whether or not their private information is on the market.
Is it truly secure, what darkish internet web sites exist, and the way do you entry the darkish internet? Let’s discover out.
What’s the darkish internet?
The US authorities developed the darkish internet in order that spies would have a spot to speak secretly. The US army developed the Onion Router, also called Tor, and made it obtainable to the general public in 2004. By encrypting information at a number of phases, the Onion routing expertise ensures that customers stay hidden when looking the online. Much like the open internet, the darkish internet is populated by teams and people that assemble and run web sites, not all of which promote or facilitate illegal exercise.
Learn how to safely entry the darkish internet
You will need to use instruments like Tor to cover your identification and get to the darkish internet. The Tor browser works similar to different browsers, besides that the content material isn’t listed, which makes it a bit more durable to seek out issues. To get to an deal with on the darkish internet, you’ll have to have hyperlinks made up of numbers and letters, with a .onion extension on the finish.
Take into accout, although, that Tor isn’t foolproof. Due to this, it’s all the time suggested to have a VPN (Digital Non-public Community) energetic to maintain your gadget and data secure.
Furthermore, VPN is an effective various to utilizing the darknet for privateness. Each VPN and the darkish internet can be utilized to navigate round censorship, whether or not company or authorities. Nonetheless, dependable VPN companies don’t pressure customers to browse at a snail’s tempo to get safe on-line.
With ClearVPN, you’ll be able to browse the web in personal, with out the dangers and hassles of the darkish internet. The app helps you to freely entry your favourite content material regardless of your location, safely go to any assets (even on public networks), and shield your private information by hiding your precise IP deal with.
Even higher: ClearVPN comes with an adblocker to cease annoying adverts, assist internet pages load quicker, and forestall web site trackers from following you as you surf the online.
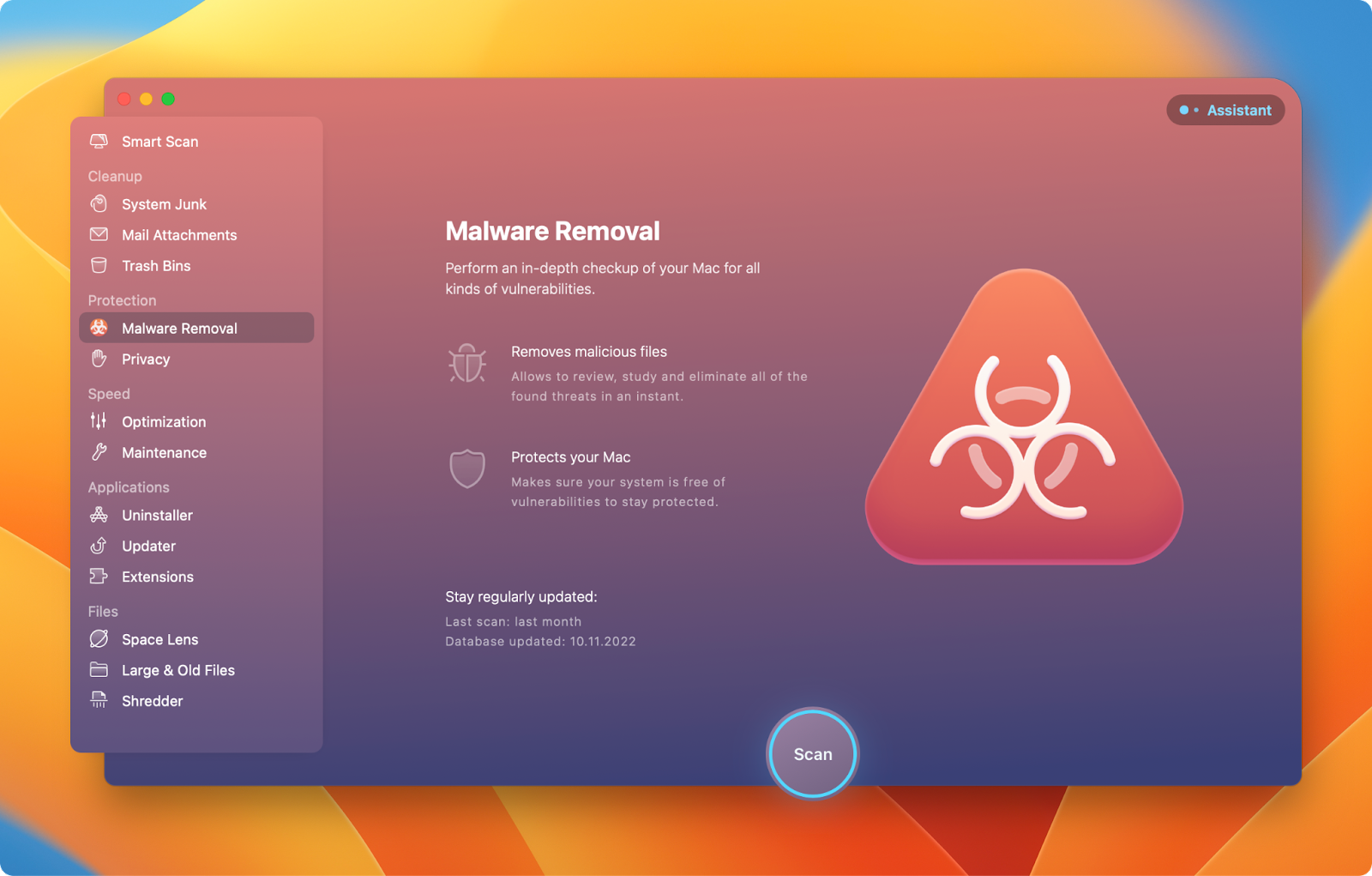
Tip: When you’re apprehensive your Mac has caught some viruses already, test it with CleanMyMac X.
Comply with the steps under to test your gadget for malware:
- Open CleanMyMac X – You may set up it from Setapp
- Select Malware Elimination from the sidebar
- Click on Scan and wait. CleanMyMac is checking for malware
- In case your Mac is contaminated, proceed with the on-screen directions after the scan is completed.
What it’s best to find out about web sites on the darkish internet
As talked about, on the darknet, you are able to do unlawful and felony issues, however you may as well discover on-line variations of books which have been out of print for a very long time, a group of political reporting from mainstream information websites, and some websites run by whistleblowers who wish to present company and authorities corruption. Listed here are a number of the methods the darkish internet can be utilized:
Anonymization
Individuals shield their on-line identities for a wide range of causes. In some circumstances, revealing their identities would put them in peril – for instance, in international locations the place the federal government prohibits all types of communication and data sharing, refugees or political outcasts looking for to attach with the skin world.
Others, reminiscent of individuals who have been cyberstalked or are involved concerning the safety of on-line banking, might use it to scale back their threat of turning into a sufferer of crime.
The Tor browser’s layered encryption system makes monitoring the identification and placement of customers inconceivable. Individuals can share recordsdata, discuss, and weblog anonymously in a extremely encrypted surroundings. Observe that the Tor browser is required to entry the darkish internet.
Accessing in style web sites
There are darknet web sites for information sources just like the BBC or New York Instances, e-mail companies like ProtonMail, and torrent websites like The Pirate Bay. More often than not, these darkish websites are for individuals who can’t get to the open internet model of the location, normally as a result of their international locations have strict web legal guidelines.
Utilizing file uploads and transfers
On the darkish internet, safe file uploads and transfers are commonplace because the onion community affords a number of ranges of encryption in your recordsdata and connection. File switch companies are used principally by journalists and informants to share delicate information-containing recordsdata.
Visiting boards and on-line chat rooms
On the darknet, there are lots of message boards and chat rooms the place individuals discuss issues that aren’t secure to speak about elsewhere on the web. Sadly, the promise of encrypted on-line exercise creates alternatives for illicit conduct. Individuals can talk about and share materials linked with illegal actions, promoting medication, weapons, and so forth.
Learn how to entry the darkish internet safely: ultimate ideas
Each Tor and VPN have their makes use of, however which one you select will depend on what you wish to do.
As a normal rule, it’s best to all the time use a VPN and solely use Tor when you should. A VPN protects your privateness with out making it onerous so that you can browse the online and use the web as you usually would. Select Tor when you should keep nameless or wish to get to the darkish internet.
If you’d like a dependable VPN, we suggest you strive ClearVPN, which is obtainable on Setapp, a platform with 240+ apps in your Mac and iPhone. CleanMyMac X, talked about on this article, can be among the many Setapp apps. Strive each for 7 days free and look into different instruments you would possibly want to enhance your workflow.

