The first utility we require to carry out our web exercise is a browser, an internet browser to be extra good by way of privateness and safety of on-line actions.
Over the Web, most of our’s exercise is logged to the Server/Consumer machine which incorporates IP handle, Geographical Location, search/exercise tendencies, and an entire lot of knowledge that may probably be very dangerous if used deliberately the opposite approach.
Furthermore, the Nationwide Safety Company (NSA) aka Worldwide Spying Company retains monitor of our digital footprints. To not point out a restricted proxy server which once more can be utilized as an information ripping server is just not the reply.
Immediately, most corporates and firms received’t will let you entry a proxy server, in case a VPN service is a dependable alternative for looking the web securely and anonymously.
So, what we want right here is an utility, ideally small in measurement, and let it stand-alone, moveable, and serves the aim. Right here comes an utility – the Tor Browser, which has all of the above-discussed options and even past that.
On this article, we can be discussing the Tor browser, its options, its usages and space of utility, set up, and different vital features of the Tor browser.
What’s Tor Browser?
Tor is a freely distributed utility software program, launched below BSD type licensing which permits one to surf the web anonymously, via its secure and dependable onion-like construction.
Tor beforehand was referred to as ‘The Onion Router‘ due to its construction and functioning mechanism, which is only written in C programming Language.
Options of Tor Browser
- Cross-Platform availability. i.e., Tor is on the market for Linux, Home windows in addition to Mac.
- Complicated information encryption earlier than it’s despatched over the Web.
- Automated information decryption on the consumer facet.
- It’s a mixture of the Firefox Browser + the Tor Mission.
- It gives anonymity to servers and web sites.
- It makes it attainable to go to locked web sites.
- Performs process with out revealing the IP of Supply.
- Able to routing information to/from hidden providers and purposes behind the firewall.
- Moveable – Run a pre-configured internet browser instantly from the USB storage gadget. No want to put in it domestically.
- Accessible for architectures x86 and x86_64.
- Straightforward to set FTP with Tor utilizing configuration as “socks4a” proxy on “localhost” port “9050”
- Tor is able to dealing with hundreds of relays and tens of millions of customers.
How Does Tor Browser Work?
Tor works on the idea of Onion routing. Onion routing resembles an onion in construction. In onion routing, the layers are nested one over the opposite much like the layers of an onion.
This nested layer is answerable for encrypting information a number of instances and sending it via digital circuits. On the consumer facet, every layer decrypts the info earlier than passing it to the subsequent stage. The final layer decrypts the innermost layer of encrypted information earlier than passing the unique information to the vacation spot.
On this strategy of decryption, all of the layers operate so intelligently that there isn’t any have to reveal the IP and Geographical location of the consumer thus limiting any probability of anyone watching your web connection or the websites you’re visiting.
All these working appears a bit advanced, however the end-user execution and dealing of the Tor browser is nothing to fret about. In actual fact, Tor browser resembles another browser (Particularly Mozilla Firefox) in functioning.
The best way to Set up Tor Browser in Linux
As mentioned above, the Tor browser is on the market for Linux, Home windows, and Mac. The consumer must obtain the most recent model (i.e. Tor Browser 12.0.6) utility from the hyperlink beneath as per their system and structure.
Alternatively, you should utilize the next wget command to obtain the tor browser instantly within the command line.
---------------- On 64-Bit System ---------------- $ wget https://dist.torproject.org/torbrowser/12.0.6/tor-browser-linux64-12.0.6_ALL.tar.xz ---------------- On 32-Bit System ---------------- $ wget https://dist.torproject.org/torbrowser/12.0.6/tor-browser-linux32-12.0.6_ALL.tar.xz
After downloading the Tor browser, extract the archive utilizing the tar command and set the execute permission to permit this system to run.
$ tar -xvf tor-browser-linux*
Observe: Within the above command we used ‘$‘ which implies that the package deal is extracted as a consumer and never the foundation. It’s strictly recommended to extract and run the tor browser as an everyday consumer.
After profitable extraction, we will transfer the extracted browser wherever within the system or to any USB Mass Storage gadget and run the appliance from the extracted folder as an everyday consumer as proven.
$ cd tor-browser/ $ ./start-tor-browser.desktop
Making an attempt to connect with the Tor Community. Click on “Join” and Tor will do the remainder of the settings for you.
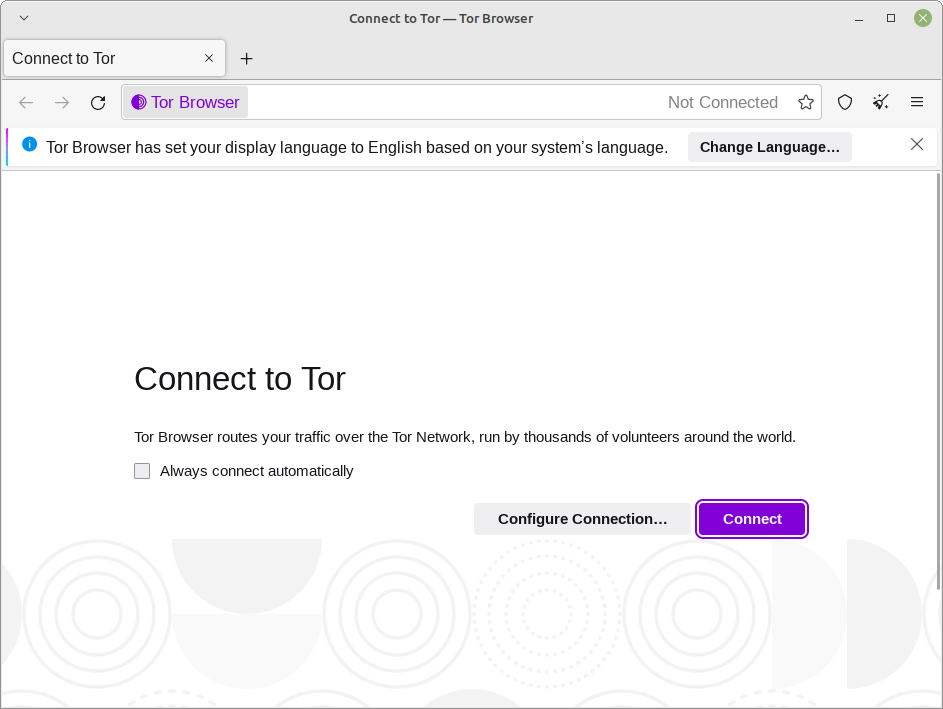
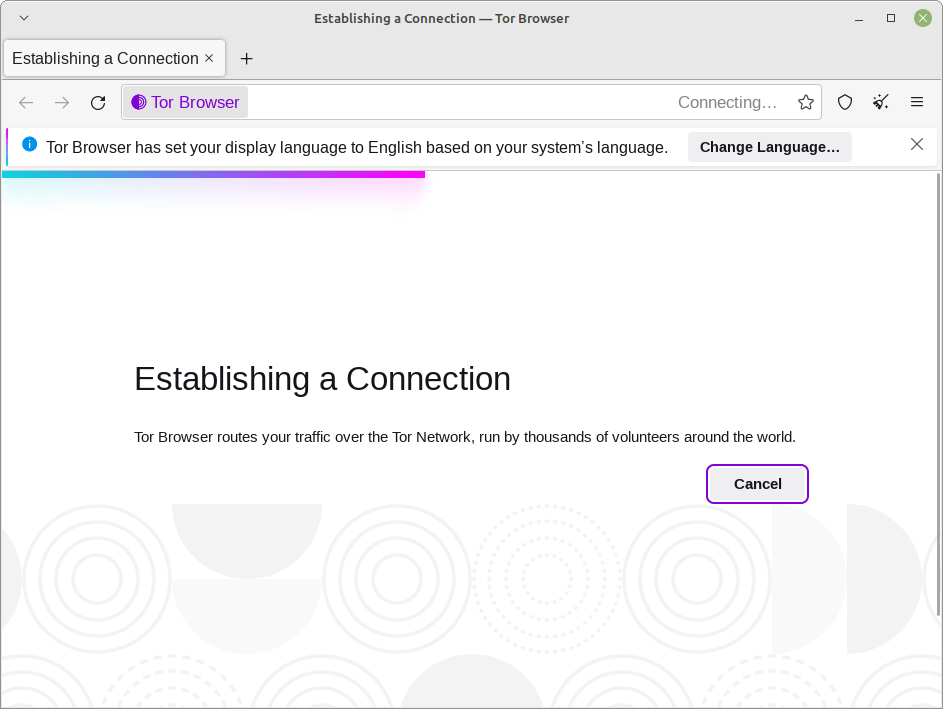
The welcome Window/Tab.
Create Tor Desktop Shortcut in Linux
Keep in mind that it’s worthwhile to level to the Tor startup script utilizing textual content session, each time you need to run Tor. Furthermore, a terminal can be busy on a regular basis till you’re working tor. The best way to overcome this and create a desktop/dock-bar icon?
We have to create tor.desktop the file contained in the listing the place extracted information reside.
$ contact tor.desktop
Now edit the file utilizing your favourite editor with the textual content beneath. Save and exit. I used nano.
$ nano tor.desktop
#!/usr/bin/env xdg-open [Desktop Entry] Encoding=UTF-8 Identify=Tor Remark=Nameless Browse Sort=Software Terminal=false Exec=/house/tecmint/Downloads/tor-browser/start-tor-browser.desktop Icon=/house/tecmint/tor-browser/Browser/browser/chrome/icons/default/default128.png StartupNotify=true Classes=Community;WebBrowser;
Observe: Be certain to switch the trail with the placement of your tor browser within the above.
As soon as achieved! double click on the file tor.desktop to fireside the Tor browser.
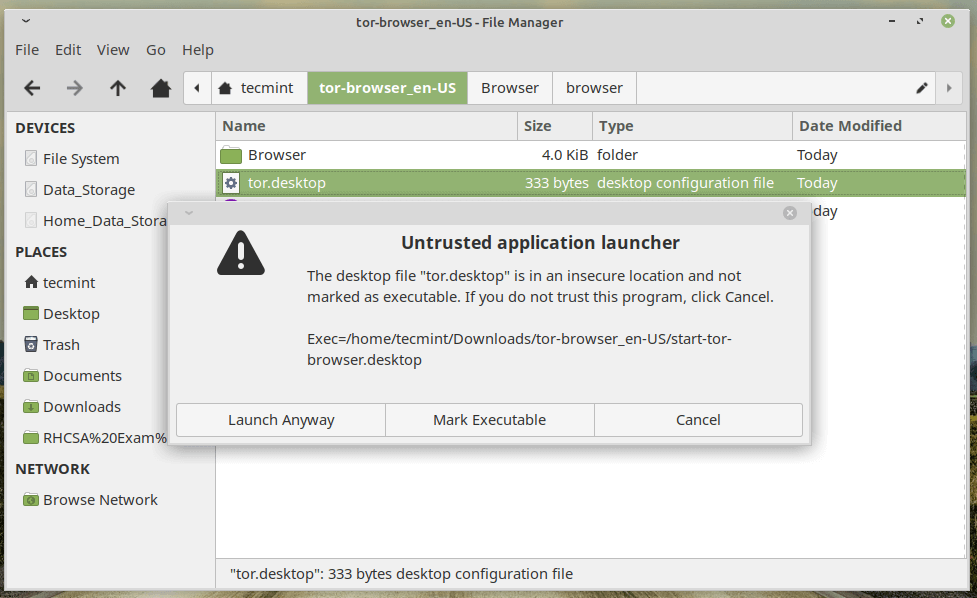
When you belief you may observe that the icon of tor.desktop modified.
You could now copy the tor.desktop icon to create a shortcut on the Desktop and launch it.
In case you are utilizing an older model of Tor, chances are you’ll replace it from the About window.
Conclusion
Tor browser is a must have instrument within the current time the place the group you’re working for doesn’t will let you entry sure web sites should you don’t need others to look into your non-public enterprise otherwise you don’t need to present your digital footprints to NSA.
Observe: Tor browser doesn’t present any security from Viruses, Trojans, or different threats of this type. Furthermore, by writing an article about this we by no means imply to bask in criminal activity by hiding our identification over the Web.
This put up is completely for instructional functions and for any unlawful use of it, neither the creator nor Tecmint can be accountable. It’s the sole accountability of the consumer.
Tor browser is an excellent utility and you could give it a attempt. That’s all for now. I’ll be right here once more with one other fascinating article you folks will like to learn.
Until then keep tuned and linked to Tecmint. Don’t neglect to supply us together with your beneficial suggestions in our remark part beneath.

