Laptop safety strategies are designed to maintain personal issues, properly, personal. There are lots of methods to safe a system. Some customers use a easy username/password login scheme for primary safety. Different customers could use additional safety by way of encryption in varied methods like utilizing VPN and disk encryption.
When you have delicate consumer information in your machine (you is perhaps working a enterprise) or materials deemed mental property or you might be privateness cautious, you might wish to contemplate disk encryption.
Some advantages of disk encryption are:
- Safe your system from hackers
- Stop information leaks
- Shield you from potential legal responsibility points
Disk encryption software program prevents a desktop exhausting disk drive, a conveyable USB storage gadget, or laptop computer, from accessing until the person inputs the right authentication information. In case your laptop computer is ever misplaced or stolen, encryption protects the information on the disk.
Nowadays, new Home windows-powered methods include BitLocker encryption by default. On Linux, LUKS is the preferred method of using disk encryption.
Questioning what’s LUKS? I am going to transient you on the subject.
Technical jargons
Earlier than going additional, some phrases must be outlined. There’s a lot to LUKS so it is going to assist to interrupt issues down, particularly if you happen to’re starting to look into this.
Quantity: A quantity is a logical storage space that can be utilized to retailer information. Within the context of disk encryption, a quantity refers to a portion of a disk that has been encrypted to guard its contents.
Parameters: Parameters are settings that management how an encryption algorithm works. Parameters would possibly embody the encryption algorithm used, the important thing dimension, and different particulars about how the encryption must be carried out.
Cipher kind: A cipher is a mathematical algorithm used for encryption It refers back to the particular encryption algorithm that’s getting used to guard the information on an encrypted quantity.
Key dimension: The important thing dimension is a measure of the energy of an encryption algorithm: the bigger the important thing dimension, the stronger the encryption. It’s usually expressed in bits, comparable to 128-bit encryption or 256-bit encryption.
Header: The header is a particular space in the beginning of an encrypted quantity that accommodates details about the encryption, such because the encryption algorithm used and the encryption keys.
The subsequent definition may be tough to a newcomer, nevertheless it’s price understanding about, particularly when coping with LUKS; it is fairly helpful.
Container: A container is a particular file that acts like a digital encrypted quantity. It may be used to retailer encrypted information, similar to an encrypted partition. The distinction is {that a} container is a file that may be saved on an unencrypted partition, whereas an encrypted partition is a portion of a disk that has been encrypted as an entire. A container, then, is a file that acts as a digital encrypted quantity.
What Is LUKS and What Can It Do?
Linux Unified Key Setup – LUKS is a disk encryption specification created by Clemens Fruhwirth in 2004 and was initially supposed for Linux. It’s a well-known, safe, and high-performance disk encryption methodology based mostly on an enhanced model of cryptsetup, utilizing dm-crypt because the disk encryption backend. LUKS can be a preferred encryption format in Community Connected Storage (NAS) gadgets.
LUKS will also be used to create and run encrypted containers. Encrypted containers function the identical stage of safety as LUKS full-disk encryption. LUKS additionally affords a number of encryption algorithms, a number of modes of encryption, and several other hash features – a little bit over 40 potential combos.
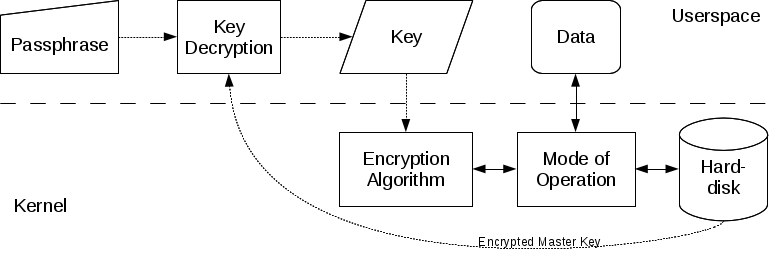
Any filesystem may be encrypted, together with the swap partition. There may be an unencrypted header in the beginning of an encrypted quantity, which permits as much as 8 (LUKS1) or 32 (LUKS2) encryption keys to be saved together with encryption parameters comparable to cipher kind and key dimension.
The existence of this header is a serious distinction between LUKS and dm-crypt, because the header permits a number of totally different passphrases for use, with the flexibility to alter and take away them simply. It’s price a reminder, nevertheless, that if the header is misplaced or corrupted, the gadget will not be decryptable.
There are two variations of LUKS, with LUKS2 having options comparable to larger resistance to header corruption, and using Argon2 encryption algorithm by default (LUKS1 makes use of PBKDF2). Conversion between each variations of LUKS is feasible in sure conditions, however some options might not be accessible with LUKS1.
The place Can I Be taught Extra?
I’m hopeful that this quick article is a assist in understanding a little bit about LUKS and encryption. The precise steps for creating and utilizing an encrypted partition with LUKS varies, relying on a person’s particular wants, so I cannot cowl set up and setup right here.
If you need a information to guide you although establishing LUKS, a wonderful information may be discovered on this article: Primary Information To Encrypting Linux Partitions With LUKS. If you happen to’re new at this, and also you wish to check out LUKS, protected studying may be executed on a digital machine or a spare laptop to get a really feel for the way it works.

